Using PowerShell to enable AutoFailback on clustered roles (or VMs in this case) was a procedure I couldn’t find online recently, so I figured I’d fiddle with it until I got it working myself.
First define the names of the roles you want to adjust. In my case, I wanted to configure this for all VMFleet VMs that I’d created for stress-testing, but I wanted to ensure they failed back if or when I rebooted a node, otherwise I’d have to initiate the moves manually should I want to run another post-tweak test.
|
1 |
$vms = Get-ClusterGroup | ? Name -match "vm-base" |
For each cluster group in that list, set the autofailbacktype to 1
|
1 |
$vms | % {$_.autofailbacktype = 1} |
That’s it. You can check that it worked by running:
|
1 |
Get-ClusterGroup | select Name,AutoFailbackType |
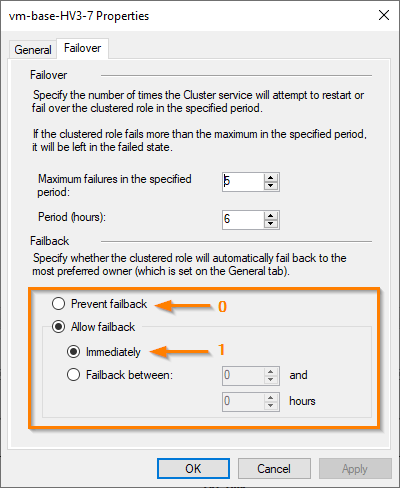
or by opening the role properties in Failover Cluster Manager and looking at the Failover tab: